Waking up to find your company on the front page news and at the center of a data breach is every CEO’s worst nightmare—and for a number of businesses, it has become reality. Today, the threats from cybercrime are real and frightening, and the risks are extraordinary. Cybersecurity is an incredibly complex issue and business leaders are grappling with how to best protect their businesses, understand the new business vulnerabilities, and identify what steps they can take to protect themselves and their customers from becoming a victim of cybercrime.
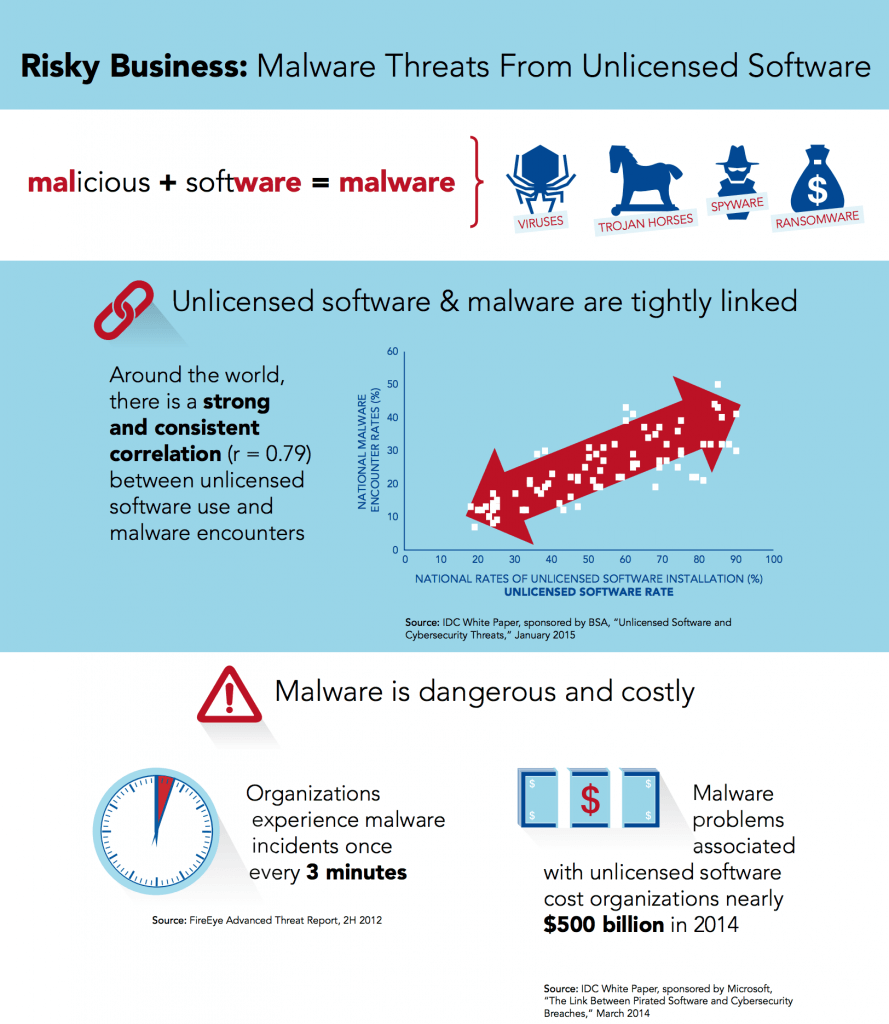
There is a strong case for organizations to put protection from malware at the top of their risk agenda. In the past year, 43% of companies experienced a data breach. The average organization experiences a malware event every three minutes, and the costs of dealing with that malware can be astronomical. The International Data Corporation (IDC) estimates that enterprises spent $491 billion in 2014 as a result of malware associated with counterfeit and unlicensed software.
A threshold step to mitigating risk is gaining an understanding of your own network and if the software you are using is genuine and fully licensed. Unfortunately, many businesses are failing to take this basic and critical first step to protect themselves.
It has long been suspected that there is a connection between unlicensed software and cybersecurity threats. A new study commissioned by BSA | The Software Alliance and conducted by IDC confirms this as fact.
The study compared rates of unlicensed software installed on PCs with a measure of malware incidents on PCs across 81 countries. Given that 43% of the software installed on PCs globally in 2014 was unlicensed, it’s clear that many businesses are at risk. The findings were sobering. The implication for governments, enterprises and consumers is clear: assessing what is in your network and eliminating unlicensed software could help reduce the risk of cybersecurity incidents.
Fortunately there are proven best practices available to tackle the challenges around software licensing. The world class standard for Software Asset Management is ISO/IEC 19770-1:2012. The importance of implementing internal controls for legal use of technology, including software, has become so critical that COSO now recommends it in its revised Internal Control – Integrated Framework.
While putting controls in place may sound simple, many businesses are missing this first step. Only 35% of companies have written policies requiring the use of properly licensed software. For CEOs, now is the time to start implementing best practices that will help mitigate security risks and avoid your business becoming tomorrow’s news headline. For more information on additional steps you can take, visit BSA’s website.
This post originally appeared on Risk Management Monitor on April 16, 2015.